SOC as a Service
Kerubiel in collabration with Black Cell SOC is a managed Cyber Security Operations Center which is suitable for all kind of organizations – we work with SMEs, large corporates, governmental and critical infrastructure organizations – regarldess of their size. SOC helps keeping your business information secure, as we provide a complex service package that covers all the necessary IT security tools, devices, technologies and knowledge. Our monthly fee structure provides a flexible and cost-effective solution as your company can reduce costs of IT security devices, licensing, deployment, training and continuous education of employees.
Because 100% protection can not be guaranteed, our special liability insurance will also cover the remaining gap on the shield.
A Cyber Security Operations Center, or SOC is a dedicated IT security unit within the organization, with one primary task: to prevent and eliminate cyber-security incidents.
Our company’s SOC-as-a-Service package is specifically designed for infrastructures over 500 IPs. Whether it’s protecting a critical infrastructure or complex enterprise, government environment, our incident response team has specialized experience to provide for our clients. The primary mission of the SOC is to prevent, detect and handle cyber security incidents. Accordingly, many preventive controls should be implemented during the design phase to reveal and eliminate known attack paths. Blind spots are eliminated by a variety of technical and logical solutions, so detection capabilities will be more efficient, faster, and the time needed to investigate events will minimized.
SOC as a Service methodolgy
Assessment
Based on Crown Jewels analysis or, based on existing risk assessment, we conducting a technology survey of the security toolkit associated with the systems concerned to determine their effectiveness and maturity.
Detection capabilities
As a result of the assessment, we create a detection capability matrix using a “top to bottom” or “bottom to top” approach, that is, to either tailor technologies to business needs, or to align with the needed coverage requirements based on available technologies and their maturity.
Hardening
With hardening, the systems’ exposure to cyberattacks and vulnerabilities can be substantially reduced.
SIEM implementation
The purpose of SIEM and similar systems is essentially to centrally store and analyze logs (events) and any security relevant data from hardware and software devices, operating systems, applications to ensure that security-threatening events, malicious acts are discovered. For a list of our supported SIEM systems, see the portfolio of our VAR division.
Use Cases
Use Cases (and related playbooks) means planned reactions and sequences of alarms that indicate a cyber-security incident and require immediate human or automated intervention. Our company has over 100 unique Use Cases that can be customized and also automated with a SOAR platform.
Triage
We define in the Use case matrix and the associated command register, together with IT security and operation stakeholders. the steps, actions, specific commands, queries that can be performed outside the SIEM system but on the connected data sources in case if further validation or more data is needed.
Monitoring
Our dedicated incident management (CSIRT) team is organized on three levels (L1-L3) and available 24/7/365 for effective IT security oversight and responsiveness. We provide 99.9% * availability for the devices we integrate and manage.
Reports and trackback
Incident management and reporting is provided by a framework that adapts to the customer’s technological and administrative capabilities. Regular reports, technical and executive reports on the performance and quality of the service provide a comprehensive overview.
Lessons learned
There may be cases for which there is no Use Case or so far unknown, and therefore we must update the rules, preventive and detective controls, and service defining documents to detect and respond to similar events in the future.
SOC as a Service bundles
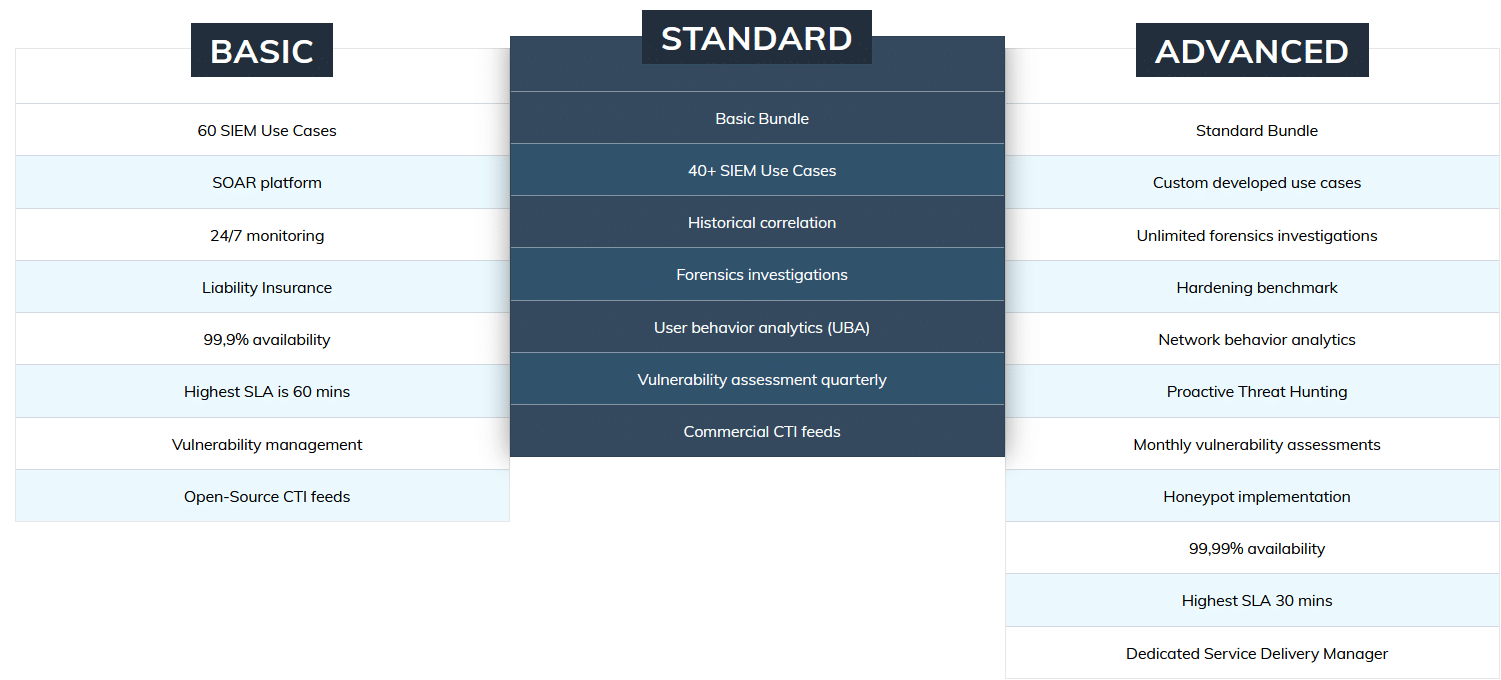
Why choose us?
Black Cell Ltd. was founded in 2010 in Hungary. The team has proven to have the right skills, competencies, and knowledgebase to successfully run and maintain a Cyber Security Operations Center. We have a strict service contract regulating our operations and also have a $1 million liability insurance. We’re operating non-stop and provide live monitoring and alarm system on each day of the year.
Our CERT team has been certified by Carnegie Mellon University. Our incident response team is made up of four experts from different IT security fields who are simultaneously serving in the SOC. These areas consist of offensive security (ethical hacking), defensive security (log analytics), threat hunting and cyber threat intelligence (CTI). In addition, our network security and product-specific support staff are also available.
Our certificates









